
Сообщений: 523
|
Опубликовано: 29.09.2014, 20:54:18
http://w4tweaks.ru/load/ here soon. Need more time for releaseДобавлено (29.09.2014, 20:53)
---------------------------------------------
 Добавлено (29.09.2014, 20:54)
---------------------------------------------
New Weapon Panel =)
|
| |
|
|

Сообщений: 6
|
Опубликовано: 30.09.2014, 02:01:47
Wow, it looks very nice. Which files are needed to replace?
|
| |
|
|

Сообщений: 523
|
Опубликовано: 05.02.2016, 22:59:18
For effect like this need change exe. But is chance that this option be in W3Dlauncher by AlexBond.Добавлено (05.02.2016, 22:59)
---------------------------------------------
End of session... It's time for small update).
|
| |
|
|

Сообщений: 523
|
Опубликовано: 04.05.2016, 00:22:54
Update:
New weapons have strange issue to not work in random crates. After careful analysis I found this functions in exe:
Function from first screen shows, where is holded data for all Q in Worms 3D. Q hold informations about: Weapon
amount, Crate chances, and Weapon delay.
On the last two screens is function, what load chances to adresses what are used by CrateRandomizer.
IfChancesNotLoaded is true(So when we don't make any changes in GM.Scheme), then game use standard chances for
crates, otherwise take data from adresses->Q.
Problem with Crate chances can be seen on third screen, where some weapons not have comparision to adresses.
The only way to bring this weapons to the pool is change exe, so this what I do:
I replace orginal data with specific jump to new allocated memory what allow me to add extra code to function,
and replace zeros with Q adresses:
For test was added only two weapons: Napalm Strike, and Super Banana Bomb
First Script: Replace third screen code:
define(address,"Worms3D.QuantifySetThreadName"+327A7)
define(bytes,74 09 8B 52 1C 89 15 58 E6 7A 00 89 1D 60 E6 7A 00 89 1D 68 E6 7A 00)
[ENABLE]assert(address,bytes)
alloc(newmem,$1000)
label(code)
label(return)
newmem:
code:
je 0B56000B
mov edx,[edx+1C]
mov [007AE658],edx
mov edx,[eax+0000004C] {Napalm Code}
cmp [edx+20],ecx
je 0B56001C
mov edx,[edx+1C]
mov [007AE660],edx
mov edx,[eax+00000070] {SBB Code}
cmp [edx+20],ecx
je 0046691E
mov edx,[edx+1C]
mov [007AE668],edx
jmp return
address:
jmp code
nop
nop
nop
nop
nop
nop
nop
nop
nop
nop
nop
nop
nop
nop
nop
nop
nop
nop
return:
[DISABLE]address:
db bytes
dealloc(newmem)
Second Script: Replace Second screen code:
define(address,"Worms3D.QuantifySetThreadName"+32B27)
define(bytes,8B 98 AC 00 00 00 39 4B 20 74 06 89 15 58 E6 7A 00 33 DB 89 1D 60 E6 7A 00 89 1D 68 E6 7A 00)
[ENABLE]assert(address,bytes)
alloc(newmem,$1000)
label(code)
label(return)
newmem:
code:
mov ebx,[eax+000000AC]{Nuclear Bomb code}
cmp [ebx+20],ecx
je 0B570011
mov [007AE658],edx
xor ebx,ebx
mov ebx,[eax+0000004C]{Napalm Strike code}
cmp [ebx+20],ecx
je 0B57001F
mov [007AE660],edx
{}
mov ebx,[eax+00000070]{SBB code}
cmp [ebx+20],ecx
je 00466CA6
mov [007AE668],edx
jmp return
address:
jmp code
nop
nop
nop
nop
nop
nop
nop
nop
nop
nop
nop
nop
nop
nop
nop
nop
nop
nop
nop
nop
nop
nop
nop
nop
nop
nop
return:
[DISABLE]address:
db bytes
dealloc(newmem)
And here is video with results:
Keep calm for the next update ^^.
Добавлено (04.05.2016, 00:22)
---------------------------------------------
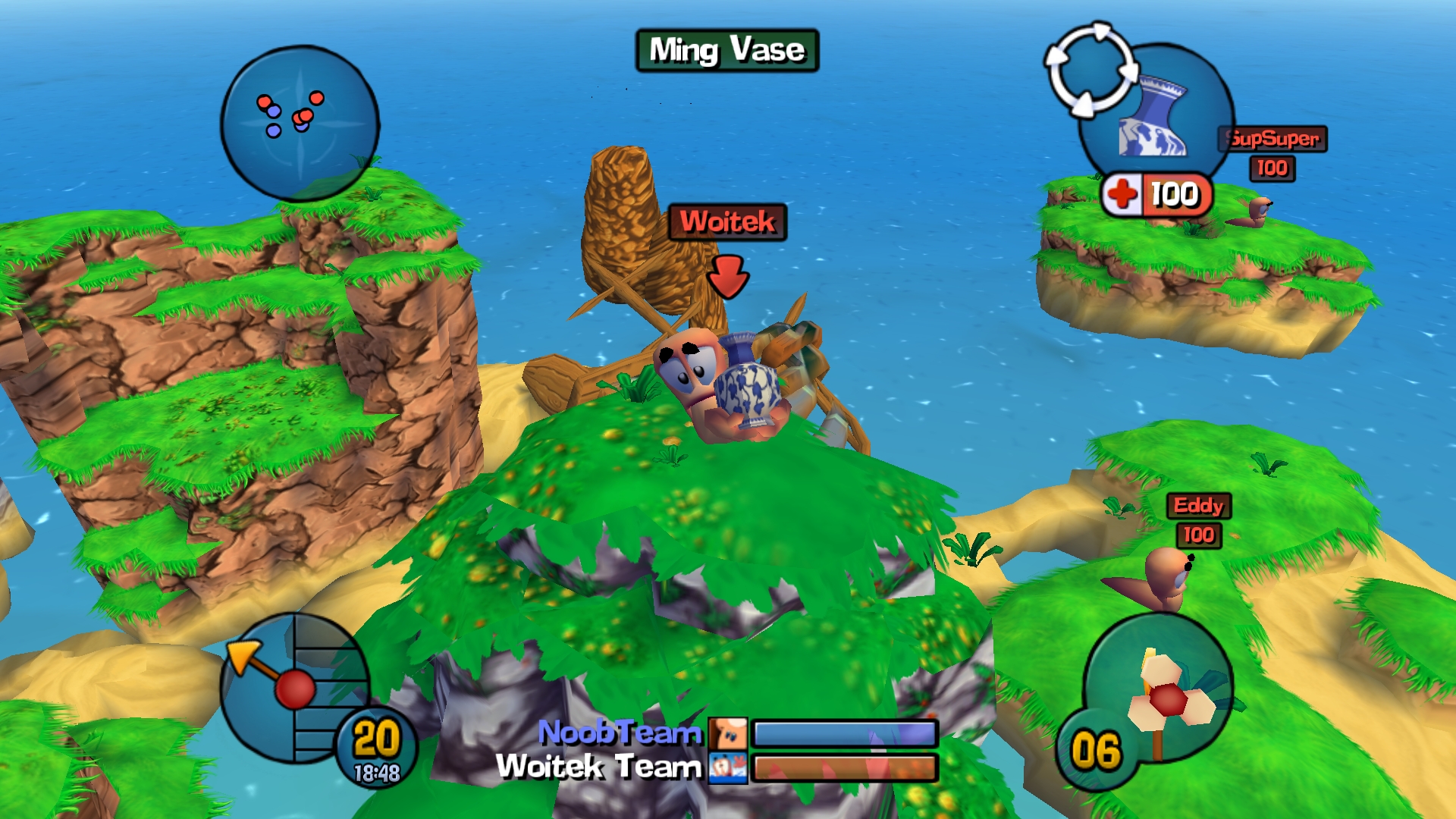
Ming Vase from Beta
Сообщение отредактировал Woitek - СР, 04.05.2016, 00:54:13
|
| |
|
|

Сообщений: 22
|
Опубликовано: 13.01.2017, 09:27:42
I still waiting for release... This mod will be "in-game realisation" of my instruction for how to hack custom schemes.
|
| |
|
|